[AF] Even though ssh Policies is disabled based on application-based ACL policy, the server still generates ssh Logs
Problem Description
AF has implemented an application-based ACL Policies to prohibit the "remote login" application Zones, but SSH error Info the server.
AF Policies configuration:
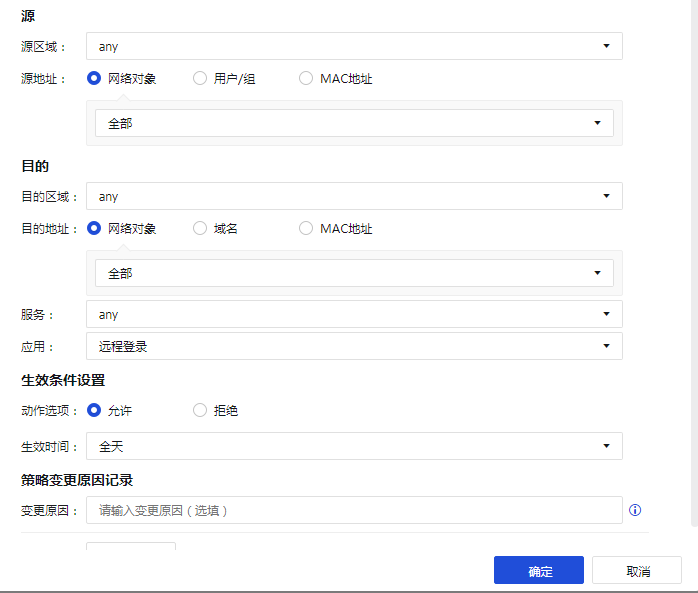
Services error Info:
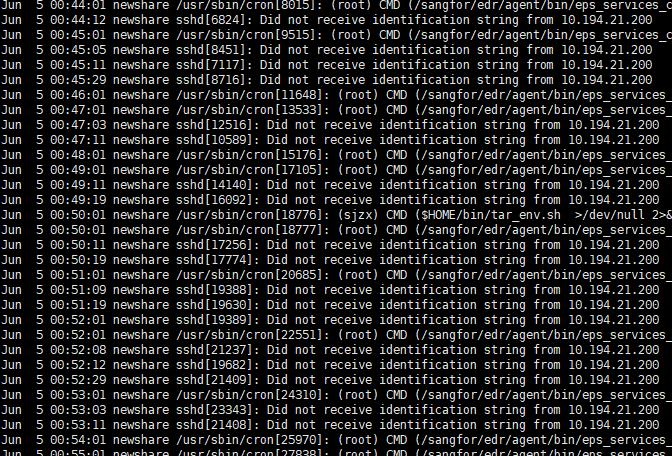
Did not receive identification string from 10. 194.21.200
Effective troubleshooting steps
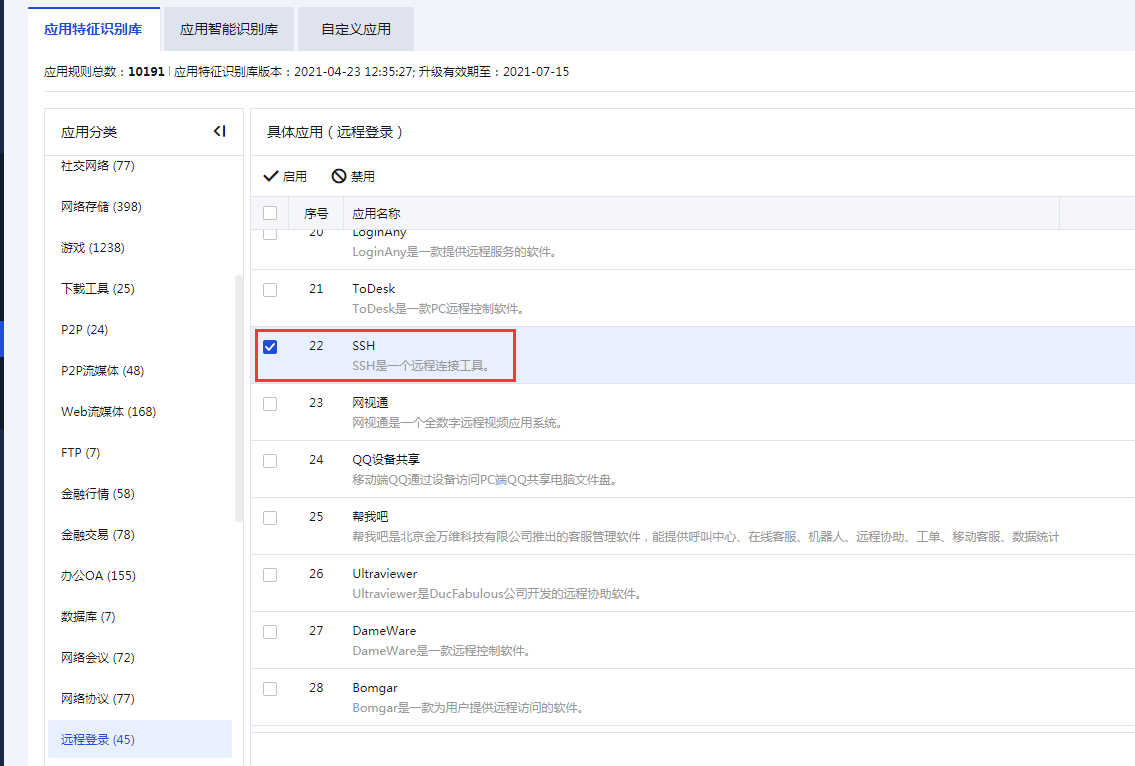
- Check whether the "Remote Login" application group contains ssh.
Confirm Sensitive. - Policies has a record Logs. Check the behavior log at the corresponding time point.
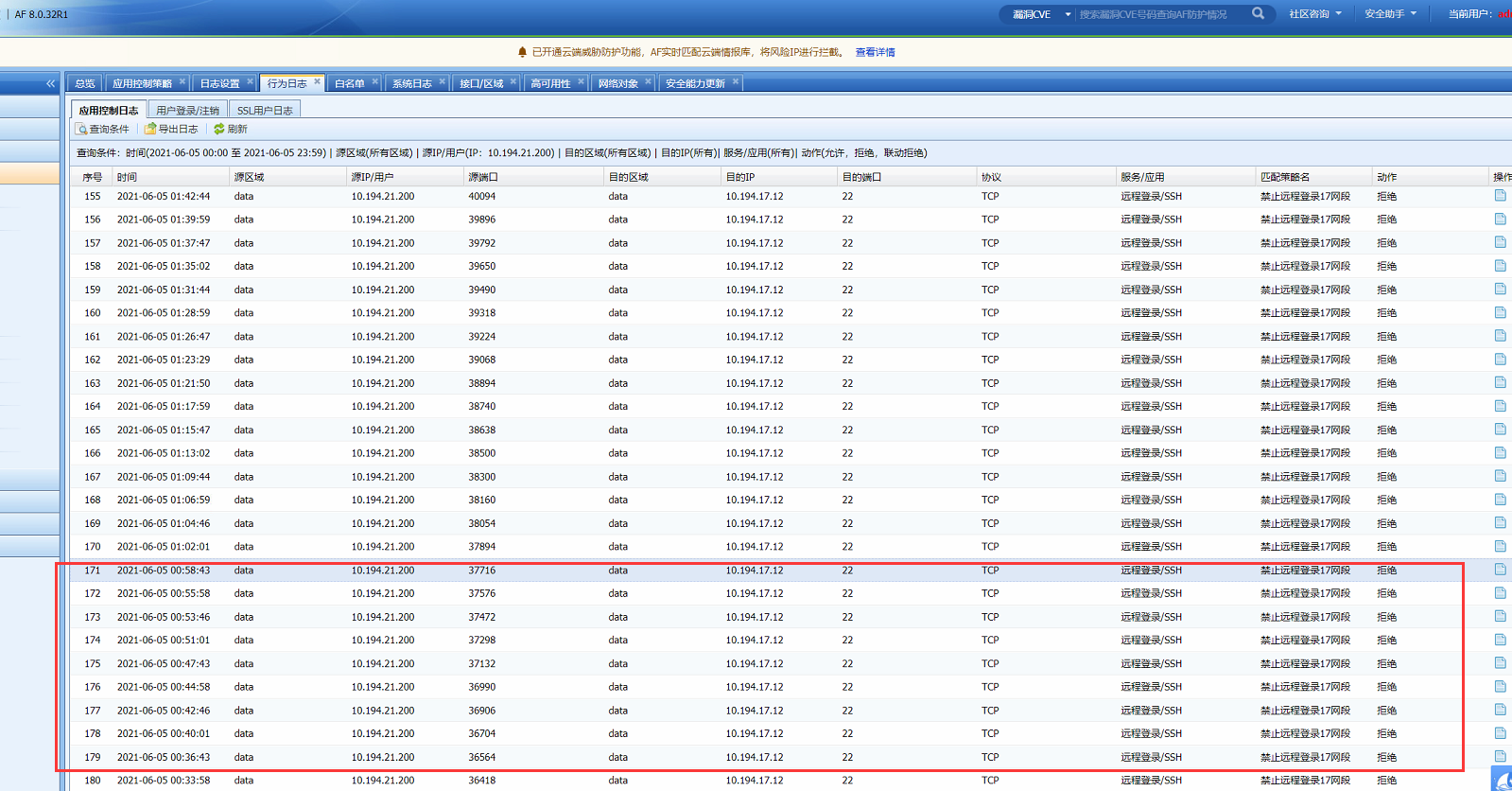
You can see the rejected logs, indicating that the interception policy at the corresponding time point is effective.
Here we think that it may be caused by the application control Policies allowing some data packets to pass. Searching for the server's error Info, I found that the meaning of this log is: This error Info means that the ssh Services is waiting because it did not receive what it needed in time. Usually due to the
Connection problem. In an ssh connection, the server first provides its identification string and then waits for the client to provide its identification string. if
_The connection is lost, or the client just quits, and what you see in the Logs occurs. _
Root cause
The application-based ACL Policies allows the three-way handshake and Obtain the data packets after the handshake for application identification. This causes Services server to receive the handshake packet connected to the SSH port. After Services server sends back the packet, the subsequent interaction is recognized and intercepted by AF. So this error occurred.
solution
In scenarios where traffic restrictions are strict, it is recommended to use "Services" to configure ACL Policies, which can directly intercept syn packets.
Original Link
https://support.sangfor.com.cn/cases/list?product_id=13&type=1&category_id=1206&isOpen=true