【Cyber Command】CheckPoint Firewall Integration Guide_V3.0.65
Requirements
-
Only CheckPoint Firewall is supported in this document.
-
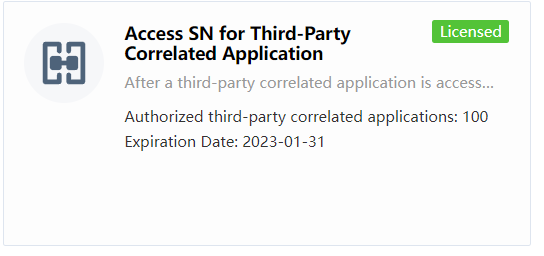
Must activate the Access SN for Third party Correlated Application.
-
The zip file application must be imported into the CC to support.
Configuration on CheckPoint Firewall
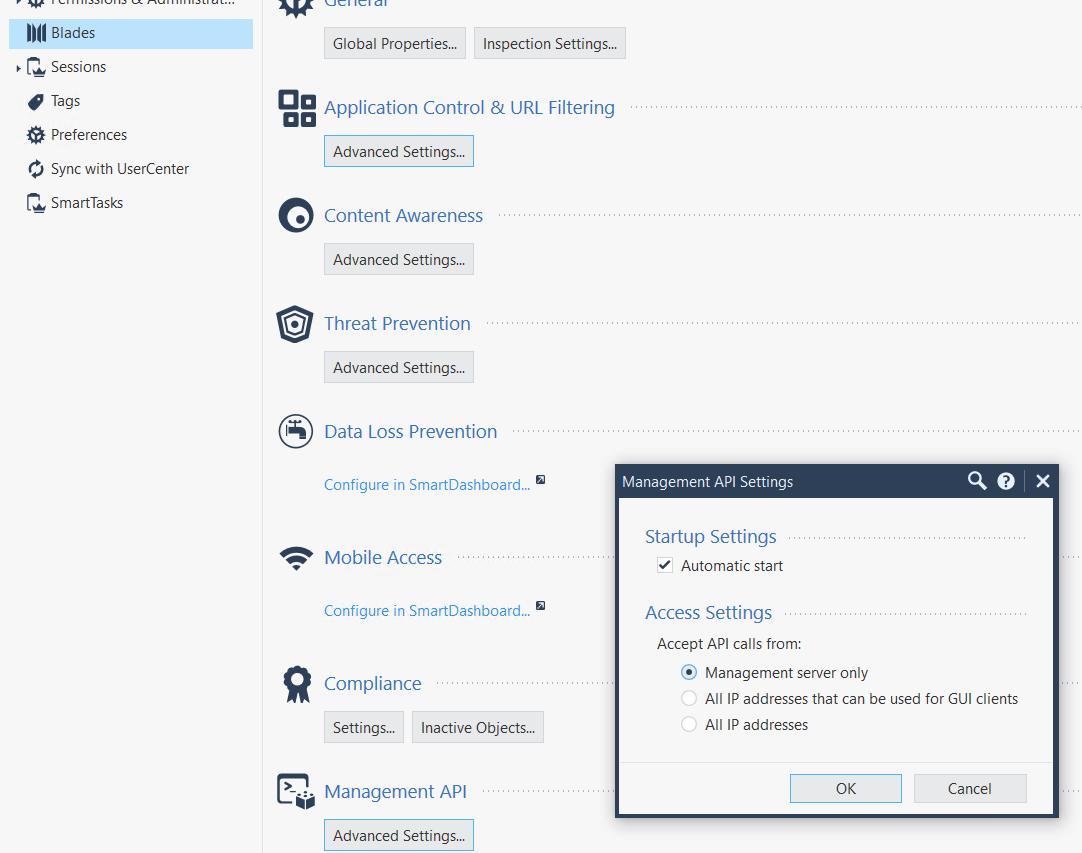
It is required to Enable the API feature on the CheckPoint firewall, as shown below.
Configuration on Cyber Command
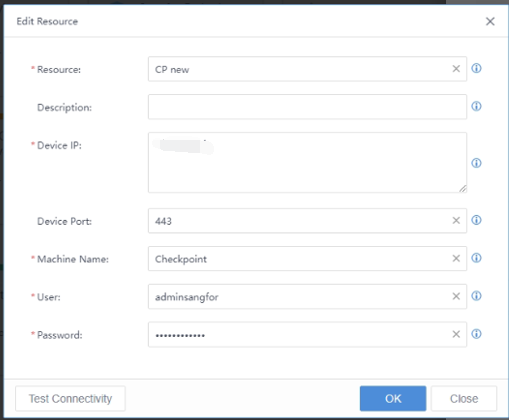
Navigate to System > Devices > Response Apps > CheckPoint to configure the CheckPoint Firewall.
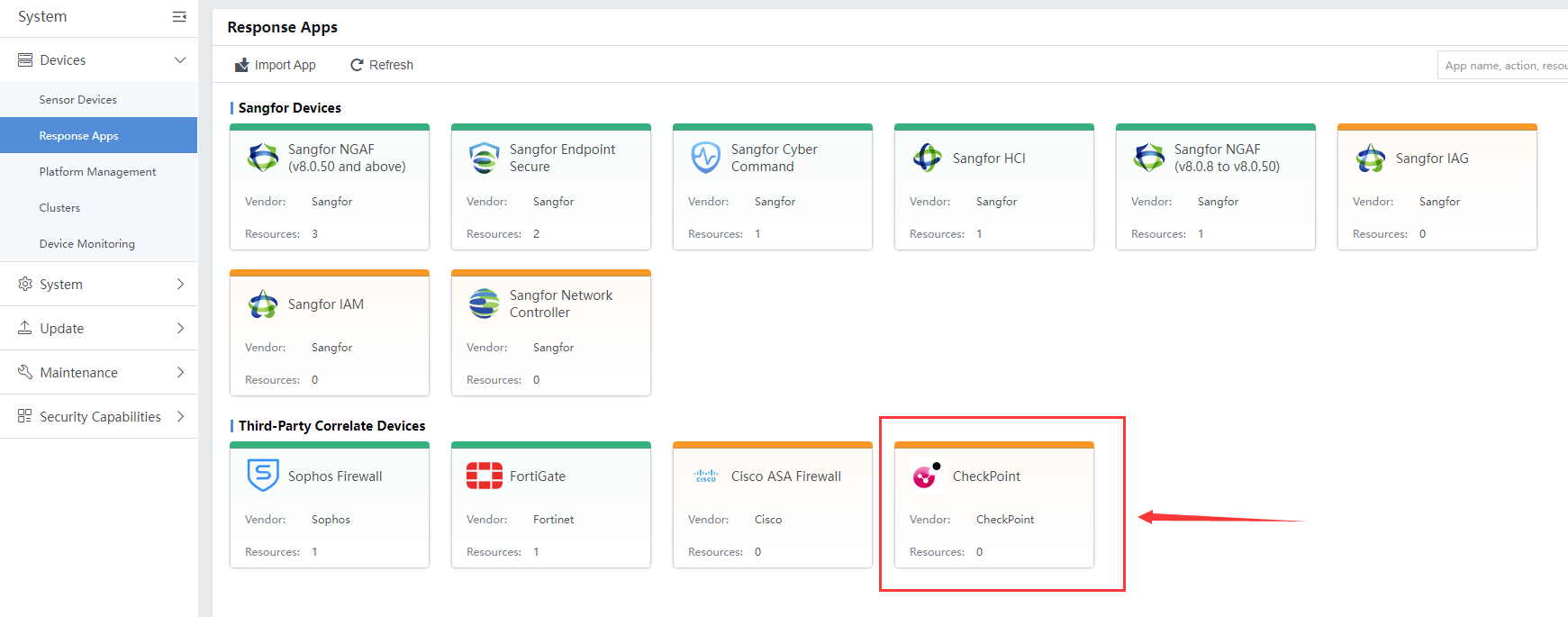
Below is an example. The device IP is the CheckPoint firewall IP address; the device port is the CheckPoint firewall’s web console listening port (by default is 443). Then, input the RESTFUL API admin and password.
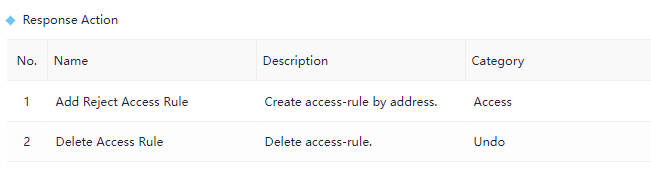
Function Supported in CheckPoint Response Apps
The supported functions are as below:
-
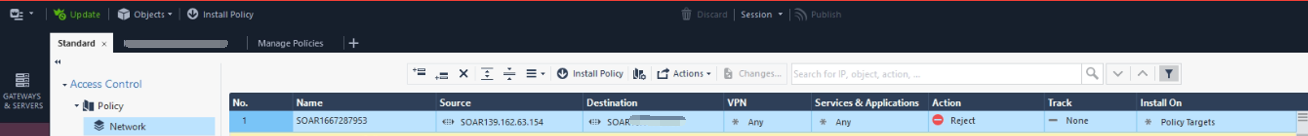
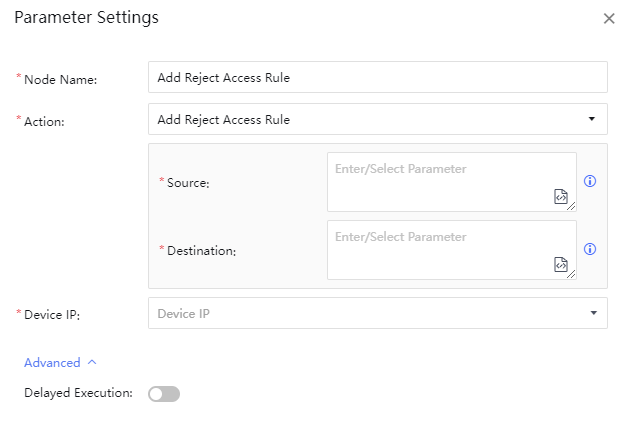
Configuring the Add Reject Access Rule can block the Source and Destination.
-
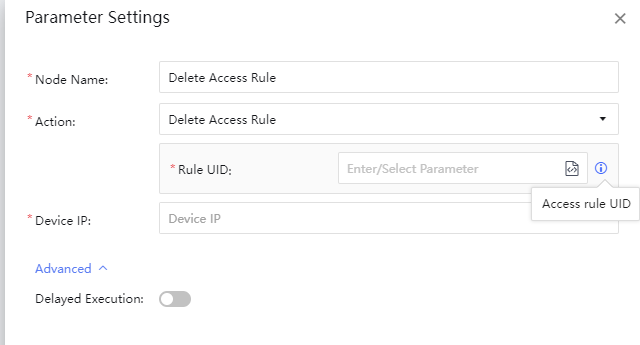
Delete Access Rule support to remove the Rule UID push from CC to CheckPoint.
Result
The newly added Rule will be added to the checkpoint’s list.