[Cyber Command] Export NGAF was detected to be infected with Cryptomining virus scanning behavior
Problem Description
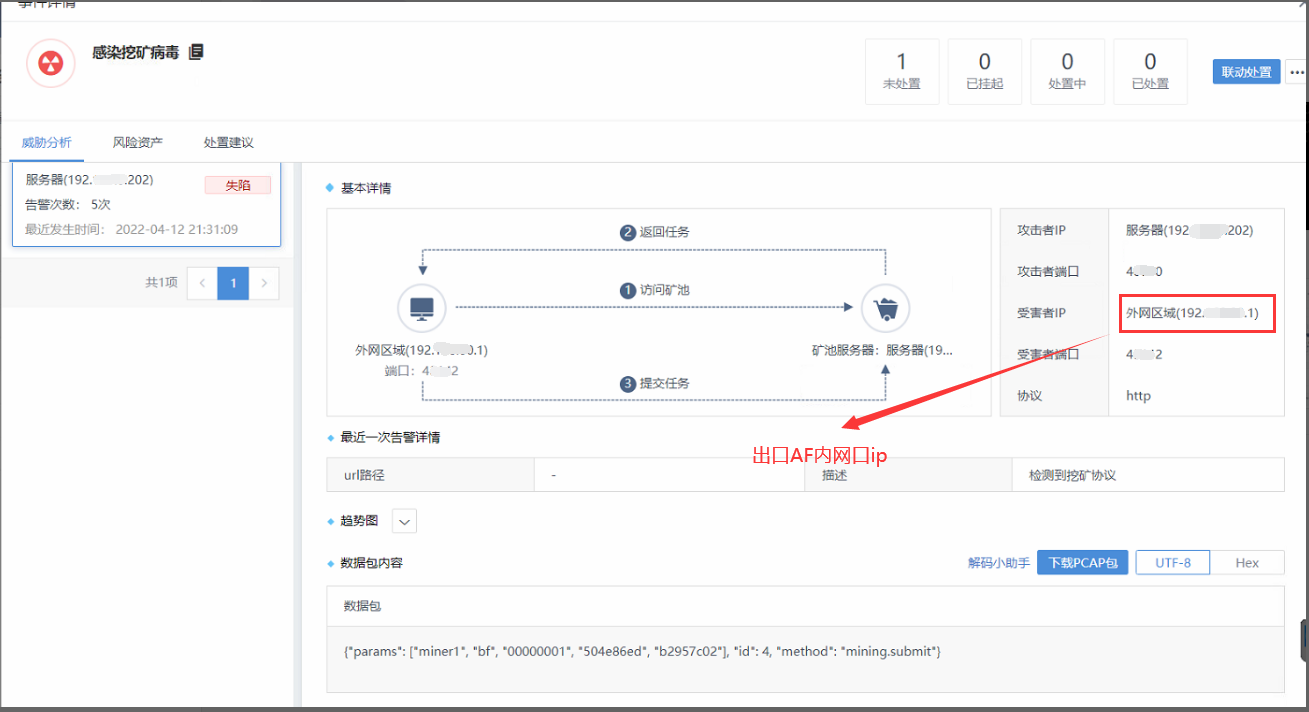
Customer feedback: In the Cyber Command Secure incident, the intranet port of the egress firewall was connected to Server, and the firewall was reported to be infected with a Cryptomining virus.
Effective troubleshooting steps
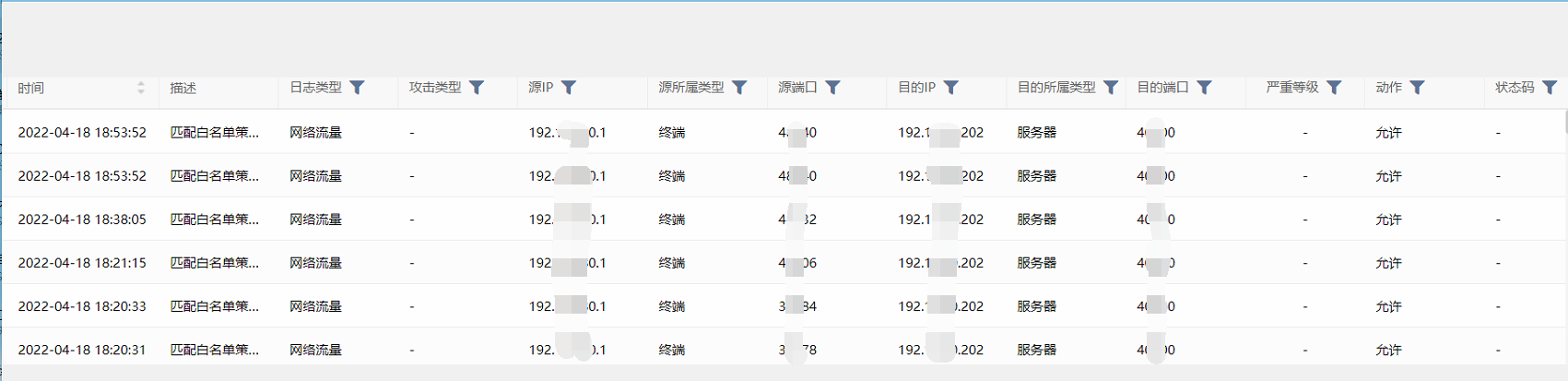
- Check raw log and find that the Dst Port is not the standard port 53, and the Dst IP is the client Server. It is speculated that the export has done Server mapping.
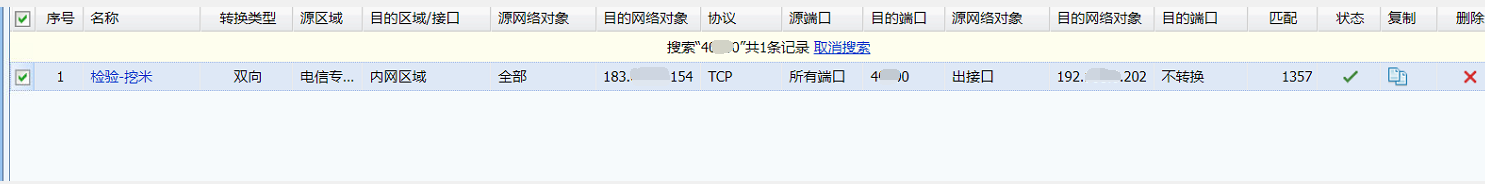
- Check the egress NGAF to confirm that bidirectional NAT is performed
Root cause
Since Server was mapped (bidirectional NAT) to the public network, the public network hacker launched a scan on the Server, and the content of the scanned data packet matched the characteristics of the Cryptomining protocol, so it was believed that LAN firewall was connecting to the Cryptomining Server (client Server).
solution
This scan does not require attention
Operation Impact Scope
no effect
Original Link
https://support.sangfor.com.cn/cases/list?product_id=24&type=1&category_id=9965&isOpen=true