[IAG] Custom URLs are identified as other applications – data is tampered by intermediate devices
Problem Description
After the policy allows the custom URL of the domain name, the webpage cannot be opened. The same policy allows the custom URL of the domain name in other branches.
Process——
- Check that the custom URL configuration is normal;
- Enable direct access and logging for the test IP. The log shows that it is identified as Application-Other and then rejected by the policy.
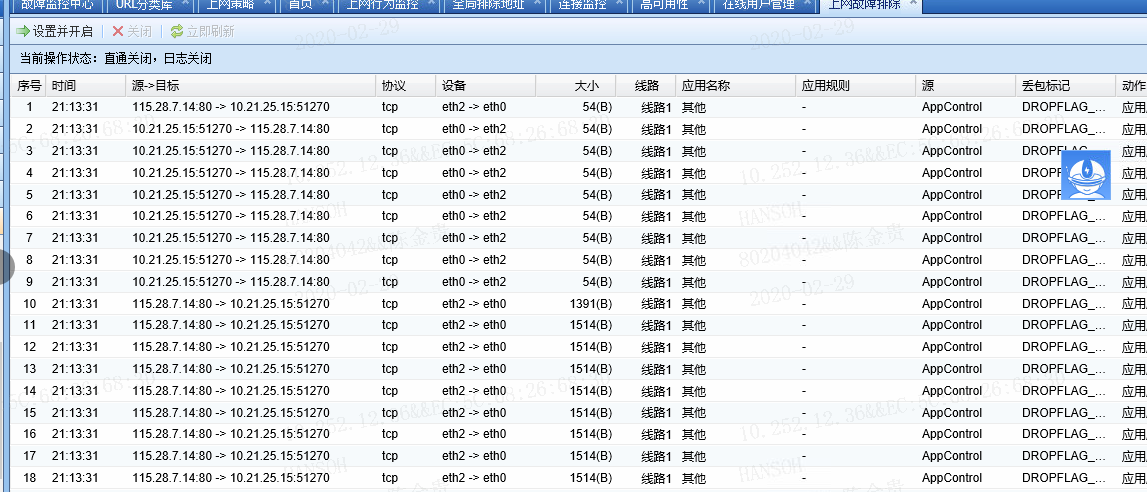
321035e5e3ce5b8f03.png (133.82 KB) - In the fault monitoring center-permission policy troubleshooting, you can see that the same destination IP and port have both records and rejection logs;
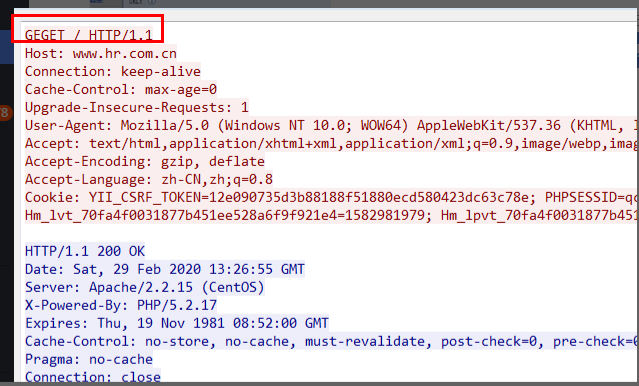
- Capture packets on the console, find the rejected requests based on the source ports that are allowed and blocked, and find that the format of the rejected requests is geget. Identify the normal requests that are allowed as get.
960015e5e3e61a94da.png (53.98 KB)
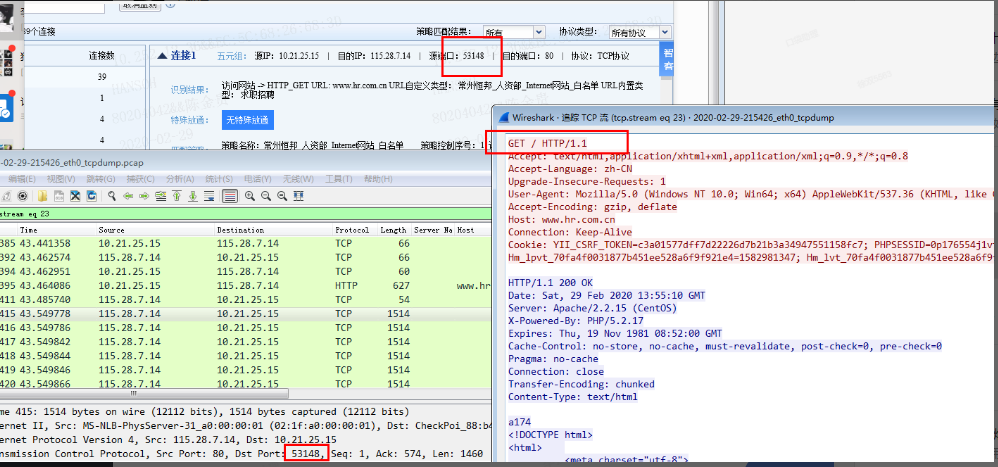
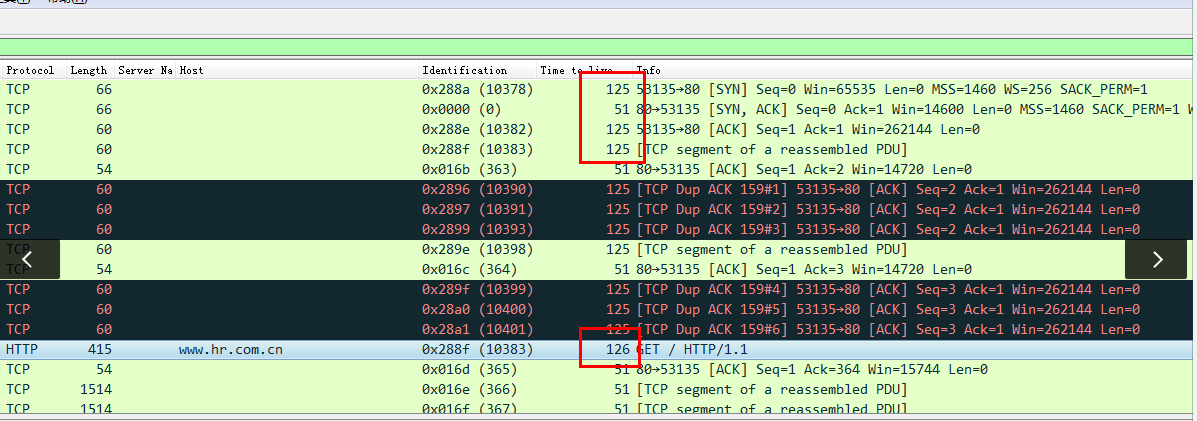
762115e5e3e8a5aa14.png (202.3 KB) - It can be clearly seen from the data packet that the ttl of the TCP connection data packet is 125, while the ttl of the abnormal request is 126. It can be inferred that the data has been tampered with by the intermediate device, making the request become an unrecognizable geget format;
897195e5e3efe60c9d.png (70.75 KB)
Root cause
The intermediate device tampered with the HTTP request, making it impossible for IAG to correctly identify the request and match it to the custom URL;
solution
- Check the security devices on the intranet that may tamper with data and adjust the corresponding policies;
- Allow custom applications to be used;
Original Link
https://support.sangfor.com.cn/cases/list?product_id=22&type=1&category_id=7285&isOpen=true