[AF] AF intercepts normal business access and logs identify it as an Information Disclosure
Problem Description
When the user accesses the URL of the internal business System is inaccessible. After checking the log of the intranet data center, an Info leakage interception log is found, as shown in the following figure:
Warning Info
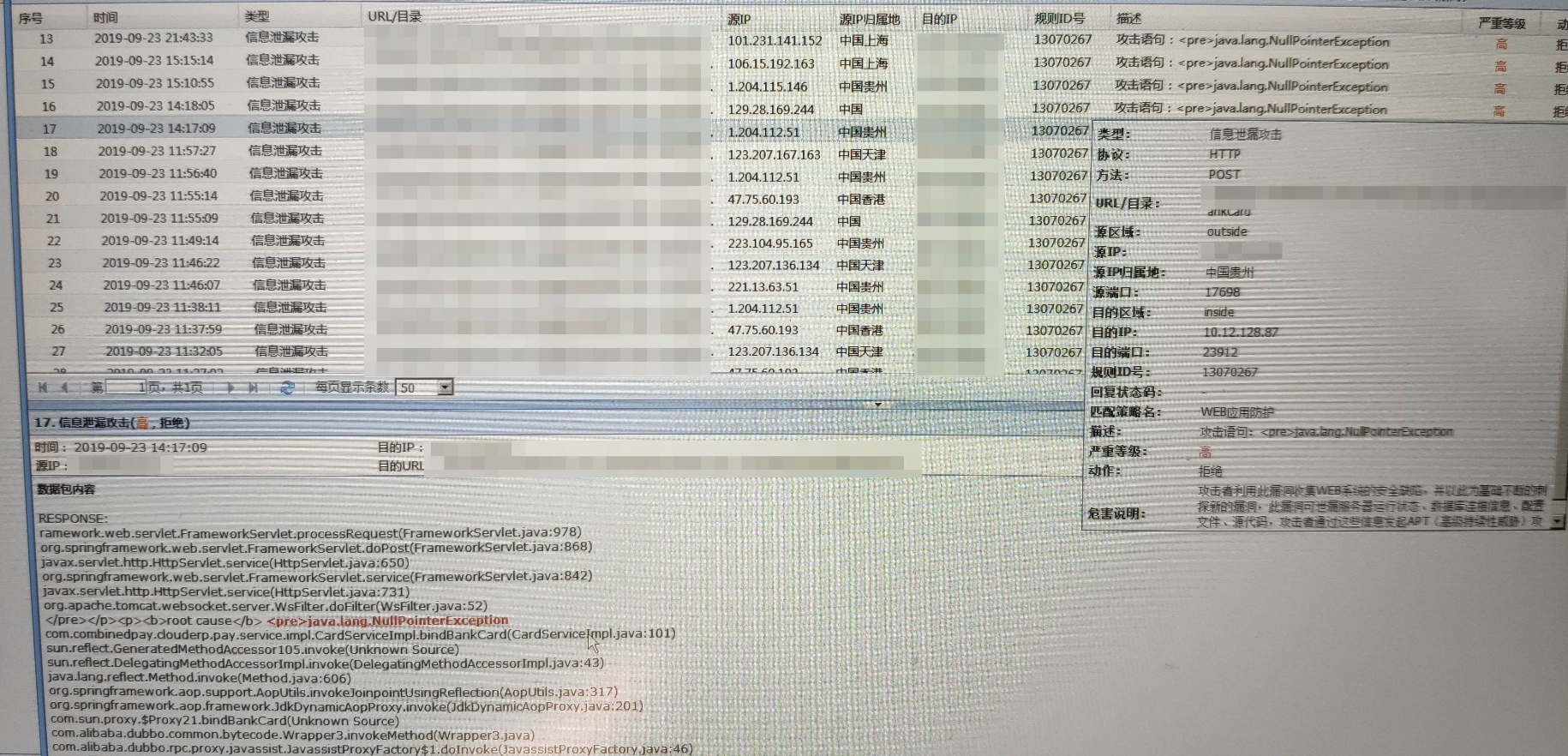
478205daef4c8b0411.png (2.5 MB)
Process——
- Take one of the Info to view detailed information, as follows:
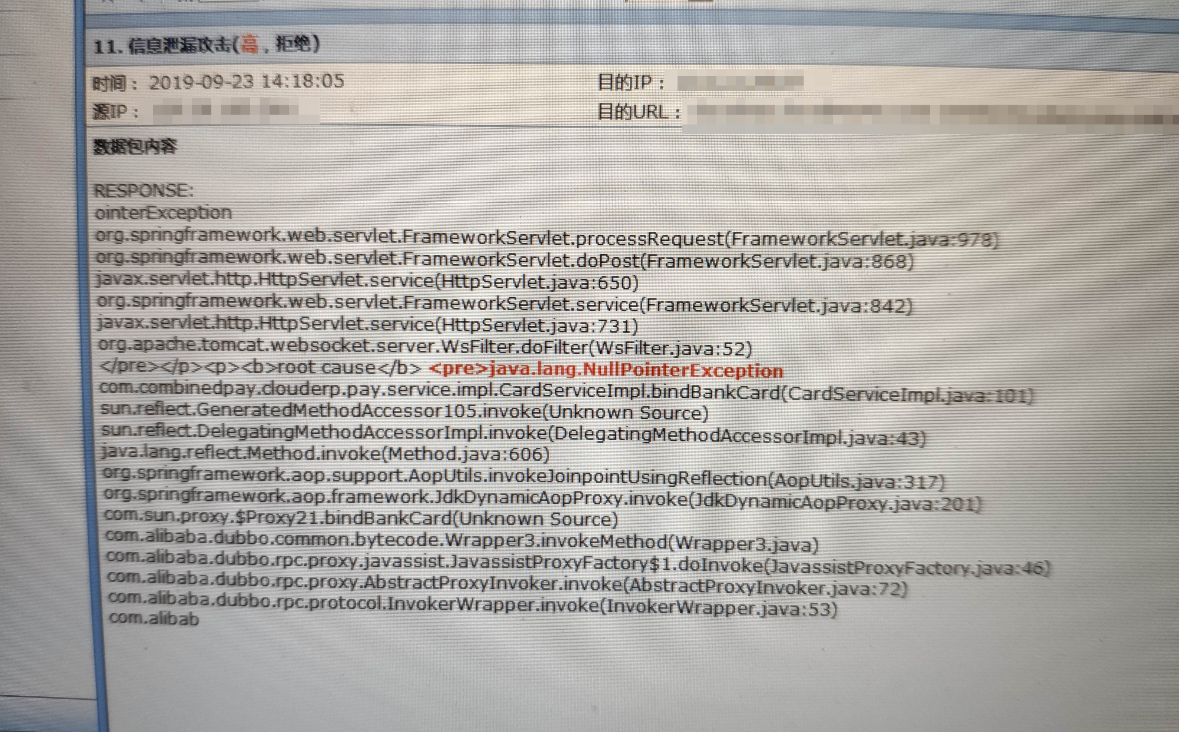
725915daef5169a418.png (1.34 MB)
The user uses the post method to send a request message to the server 10.12.128.87, but Services server's response message Sensitive null pointer exception: java.lang.NullPointerException - Check the rule id corresponding to this information: 13070267, and you can see the rule description as follows:
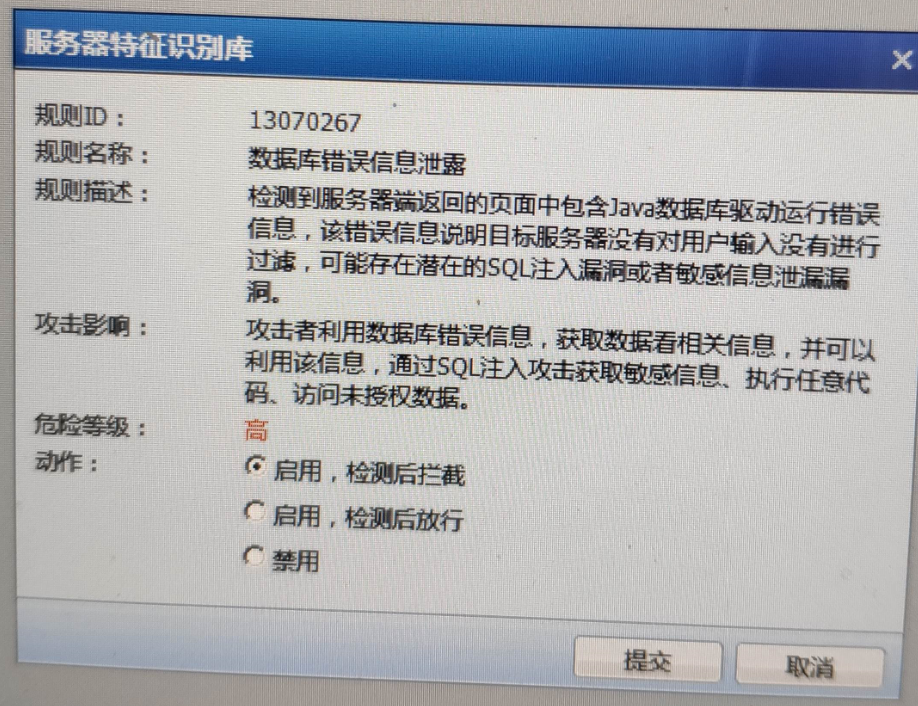
909755daef56a9f7e5.png (1.08 MB)
Root cause
Services server returns Info Medium information related to the Java database.
solution
- It is recommended to modify the System page code according to the exported attack log Info to avoid the error Info Medium Java database driver running in the server response packet, and then perform access test after the modification is completed.
- You can also exclude and release the source address, destination port, rule ID and other parameters of the specified URL according to actual needs Medium [Security Protection Strategy] – [Advanced Settings] – [Web Protection Exclusion Exclusion Settings], as follows:
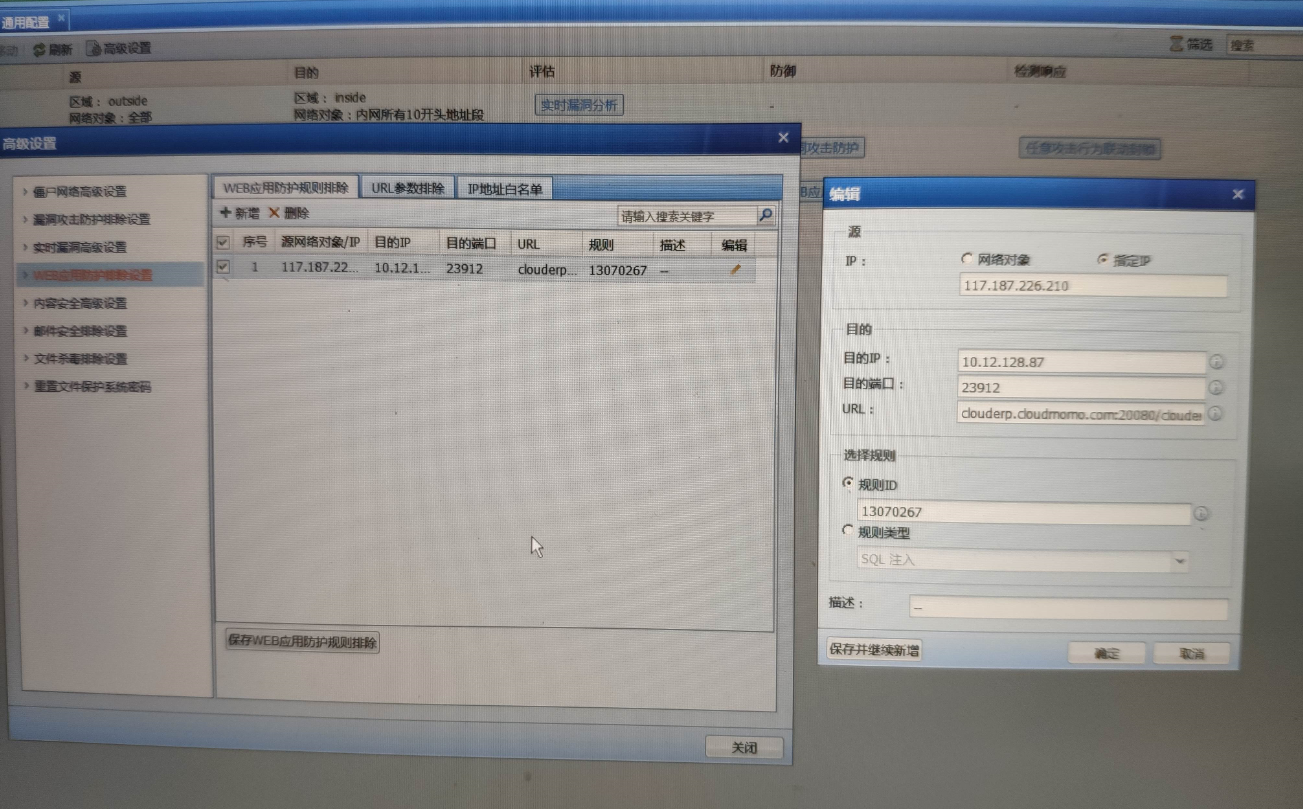
498585daef59a08a7c.png (1.31 MB)
Original Link
https://support.sangfor.com.cn/cases/list?product_id=13&type=1&category_id=736&isOpen=true