[AF] GRE access to the peer address is unavailable – caused by the peer detection mechanism
Problem Description
The GRE channel is configured and the status is displayed as normal. However, the intranet PC cannot ping the GRE peer address. The corresponding Zones the application control Policies has been allowed.
Effective troubleshooting steps
- Check Policies configuration. The GRE Tunnels Interfaces has been added to Zones and the application control policy has been configured to allow Policies to pass. After enabling application control Policies for Zones, the policy does not take effect. After enabling all Zones, the traffic becomes available. After packet capture, we can see that the data is sent but there is no response from the other end.
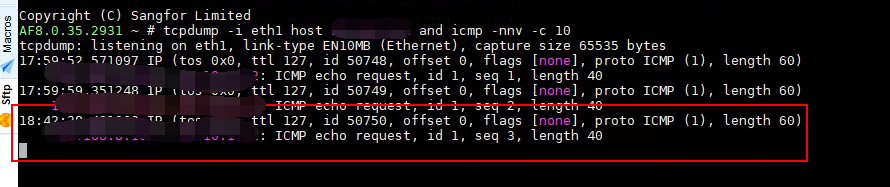
2. Further packet capture and inspection revealed that the other end had a detection mechanism. The other end must successfully detect the other end before it will respond to the packet when accessed. The order of packets sent by the other end: AF eth2 port ->gre port, and then the packets are sent back from eth2 port, but Local is not configured with the corresponding control policy to allow Policies to pass. This explains why the GRE peer address can be accessed normally when the any-to-any full-open Policies is configured.
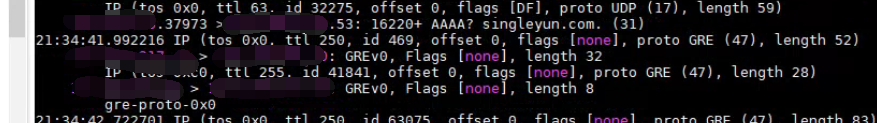
solution
Configure the application control Policies the peer GRE detection packets to pass through the Interfaces Zones and GRE Interfaces Zones.
Operation Impact Scope
N/A
Original Link
https://support.sangfor.com.cn/cases/list?product_id=13&type=1&category_id=1634&isOpen=true