[AF] IPSEC VPN cannot be established, ESP packet not received: NATT penetration is not configured
Problem Description
AF replaced H3C equipment. AF and SSL VPN were interconnected for IPSEC VPN. After the replacement, the VPN was not working; it was working before the replacement.
FW (H3C) —- Public network —- H3C (gateway) —- switch —- SSL VPN (single-arm)
Effective troubleshooting steps
- Check the dlan status of AF, it shows that the connection has been established, but it is not connected;
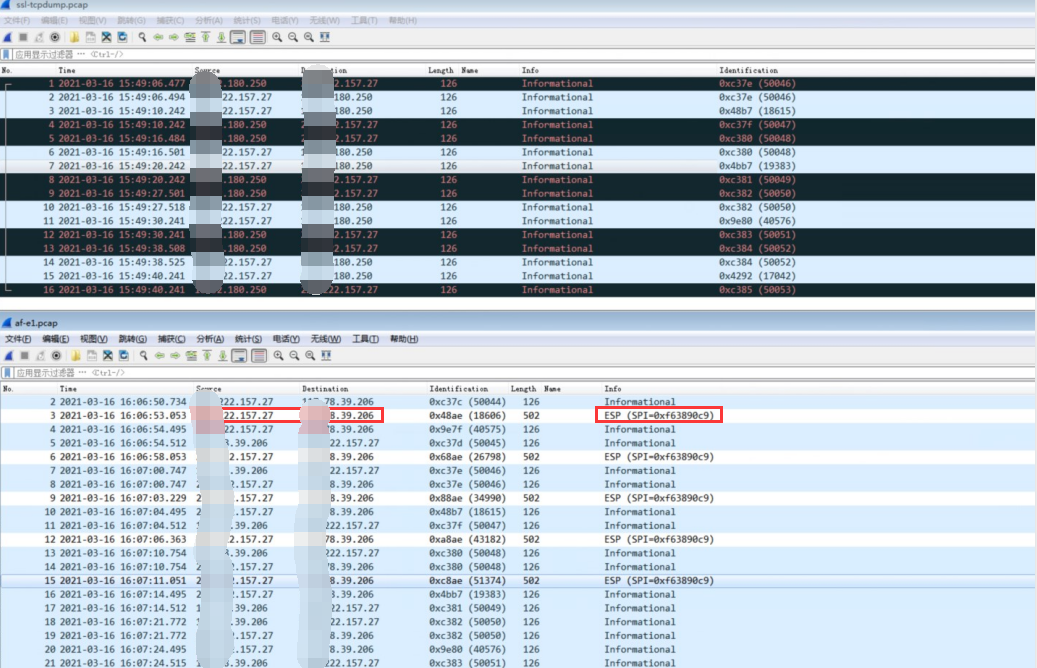
- When capturing packets between AF and SSL VPN devices, it was found that AF sent ESP packets, but the other party's SSL VPN did not receive them.
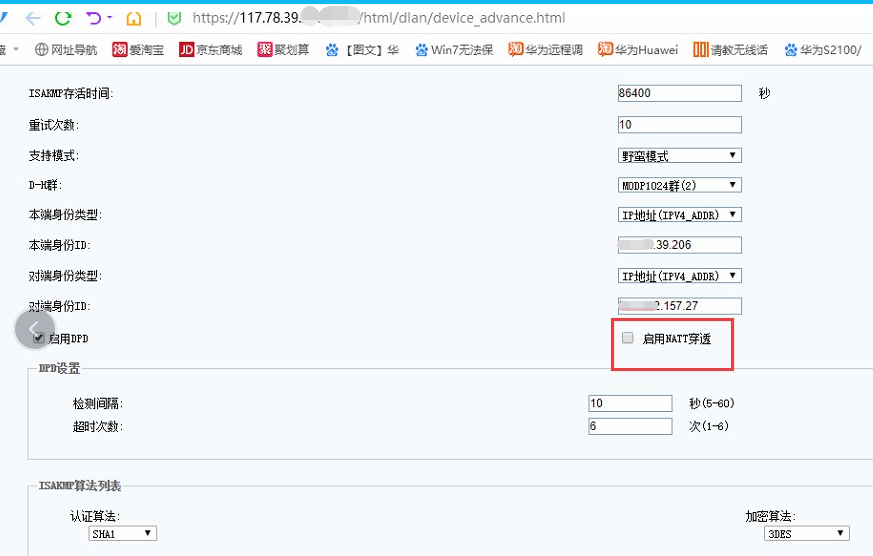
SSL was deployed in a single-arm manner on the intranet, with the front-end H3C device doing the mapping. It was found that NAT-T penetration was not checked in the IPSEC VPN settings of the SSL VPN device. After NAT-T penetration was checked on both sides, the IPSEC VPN data was connected normally when it was reconnected.
Root cause
The second stage of IPSEC VPN is transmitted through the ESP protocol. If the front-end NAT device does not do ESP mapping, it cannot penetrate; the SSL device actively sends ESP to the AF end, which can work; AF actively accesses ESP, which needs to be mapped by the front-end Local, and it will not work without mapping.
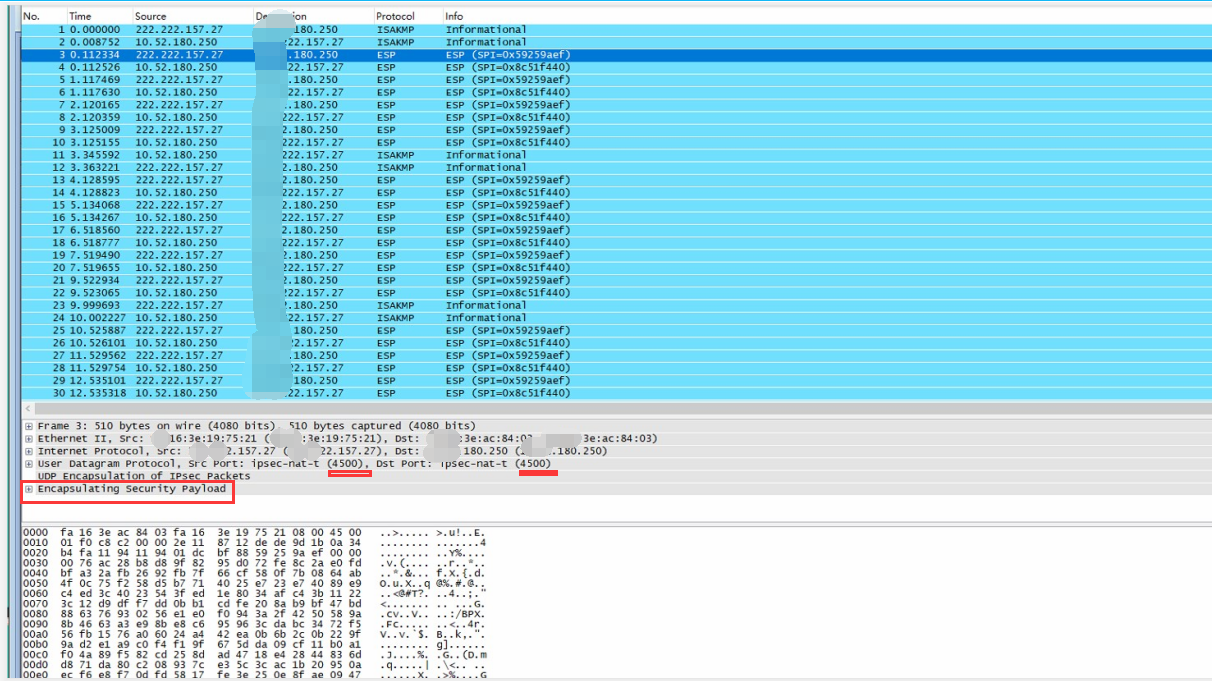
After configuring NAT-T, the ESP protocol is encapsulated in UDP 4500. UDP4500 is mapped and can be penetrated.
solution
The front-end device is not configured with ESP protocol mapping. By configuring NAT-T penetration on both sides, ESP is encapsulated in UDP port 4500, and normal communication can be achieved.
Original Link
https://support.sangfor.com.cn/cases/list?product_id=13&type=1&category_id=1167&isOpen=true