[AF] Protocol exception module interception of abnormal access through AF business
Problem Description
The access to the business page is abnormal. It is normal when direct access is enabled in AF. The direct access Logs is shown in the figure below:
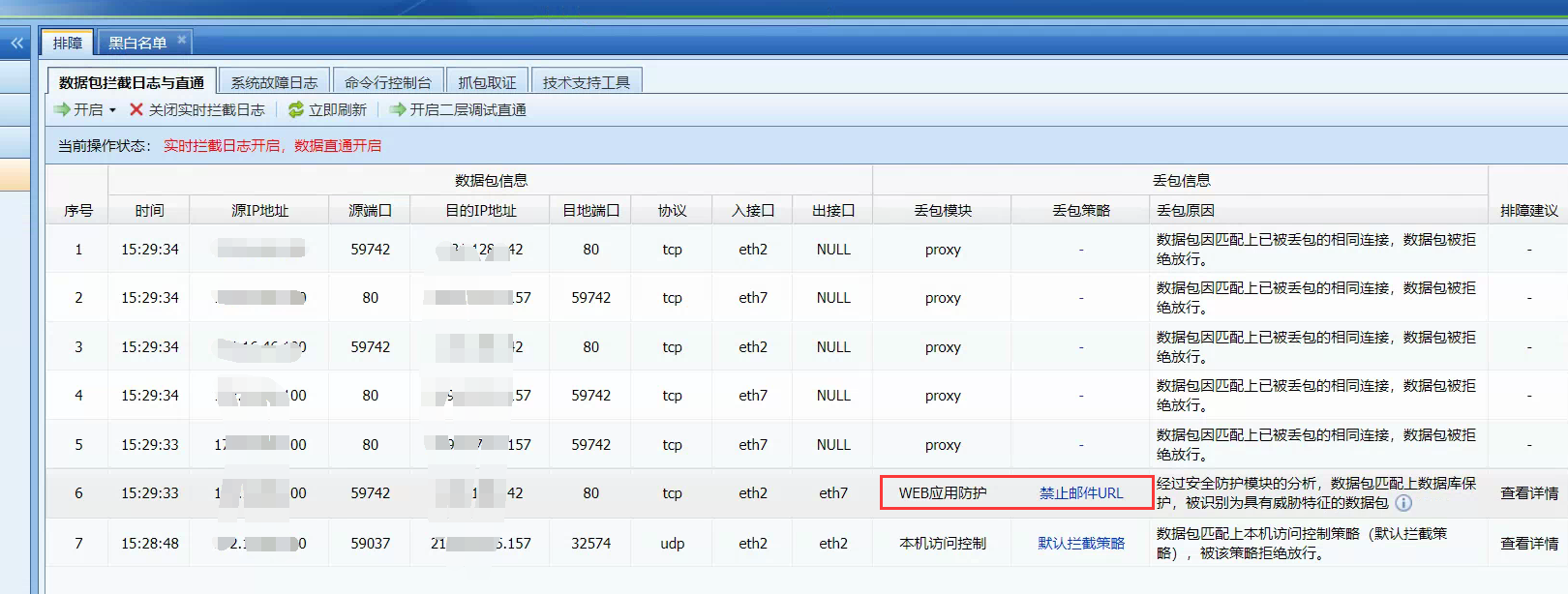
251435e7351da44886.png (475.35 KB)
Process——
- According to the direct Logs, it is determined that the Web App Firewall Policies intercepted. After checking the built-in data center Logs, it is found that it was intercepted by the [Protocol Abnormality] – [Content-Type Header Field Duplicate Detection] module, as shown in the following figure:
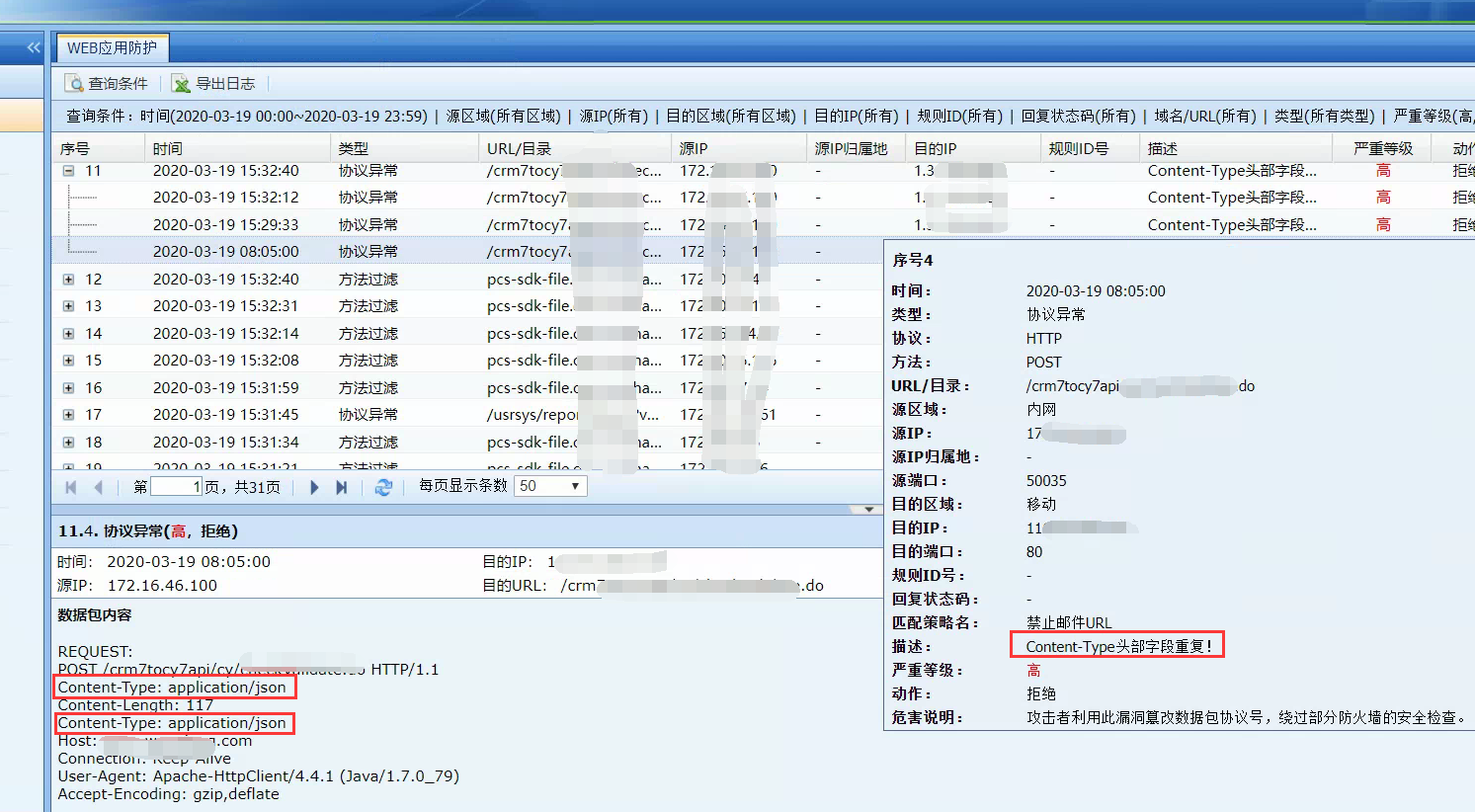
758195e73524863e2d.png (625.37 KB) - This situation is caused by repeated Content-Type header fields in the data packet, which is detected and intercepted by protocol anomaly. The conventional processing method is to adjust the server code so that the interactive data packet no longer has repeated Content-Type header fields; or after explaining the situation with the customer and reaching an agreement, disable [Content-Type header field duplicate detection]. Operation path: [Objects] – [Security Policies Template] – [Web App Firewall] to find the corresponding template, [Advanced Configuration] – [HTTP Request Anomaly], uncheck the [Content-Type header field duplicate detection] option, as shown below:
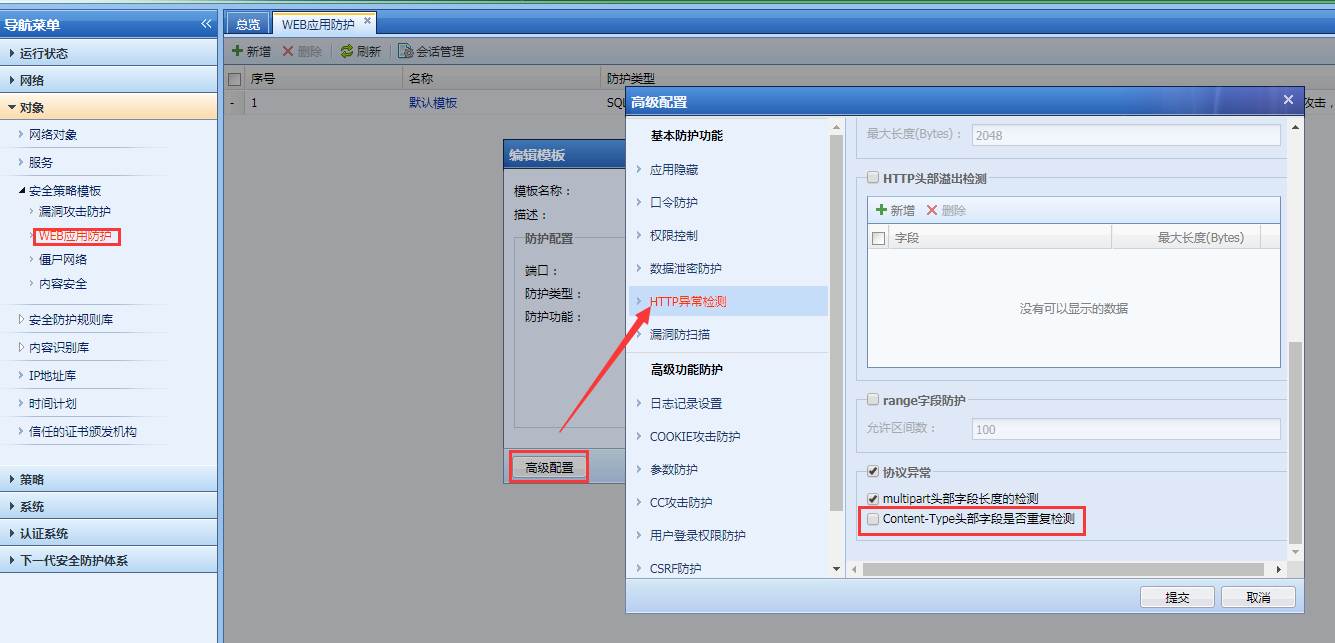
959105e7353a58e782.png (103.94 KB)
solution
- The conventional solution is to adjust the server code so that its interactive data packets no longer have repeated Content-Type header fields;
- After explaining the situation to the customer and reaching an agreement, disable [Content-Type header field duplication detection].
Original Link
https://support.sangfor.com.cn/cases/list?product_id=13&type=1&category_id=823&isOpen=true