[AF] Session Initiation Protocol detected that Local intranet port was using the intranet DNS lookup malicious domain names
Problem Description
The customer reported that Local internal network port was using the internal network DNS server to resolve malicious domain names. The Local DNS was configured with the public network 114.114.114.114
Warning Info
The log is shown below:
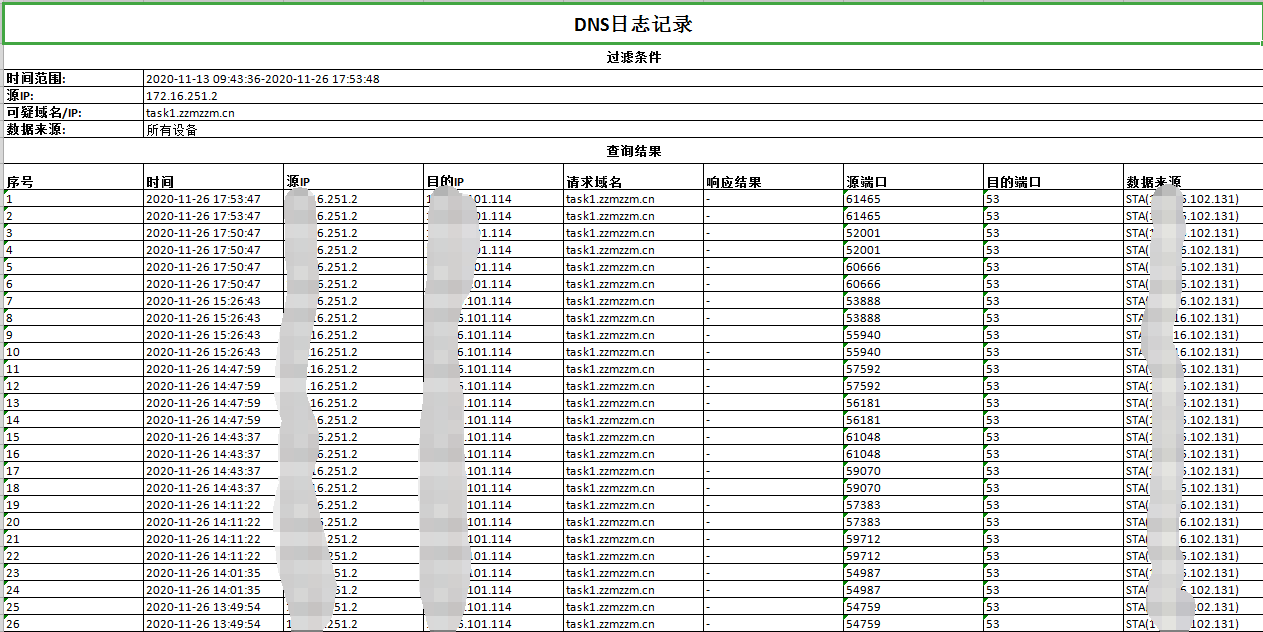
Effective troubleshooting steps
- Local itself will not actively resolve malicious domain names. First, check whether the DNS Proxy and NAT are configured to see if port 53 of the intranet DNS is mapped out;
- Check and find that common proxies are not enabled. Test access to this domain name on the Local. Capture the packet and see that it is directly resolved through the public network 114 and then sent to the public network port, which is inconsistent with the Logs description. The problem of Local itself is ruled out;
- Analysis found that the customer used the SSL VPN function, configured the Local to use the intranet port to access resources, and also enabled the intranet DNS address to resolve the domain name first. The configuration is shown in the figure below:
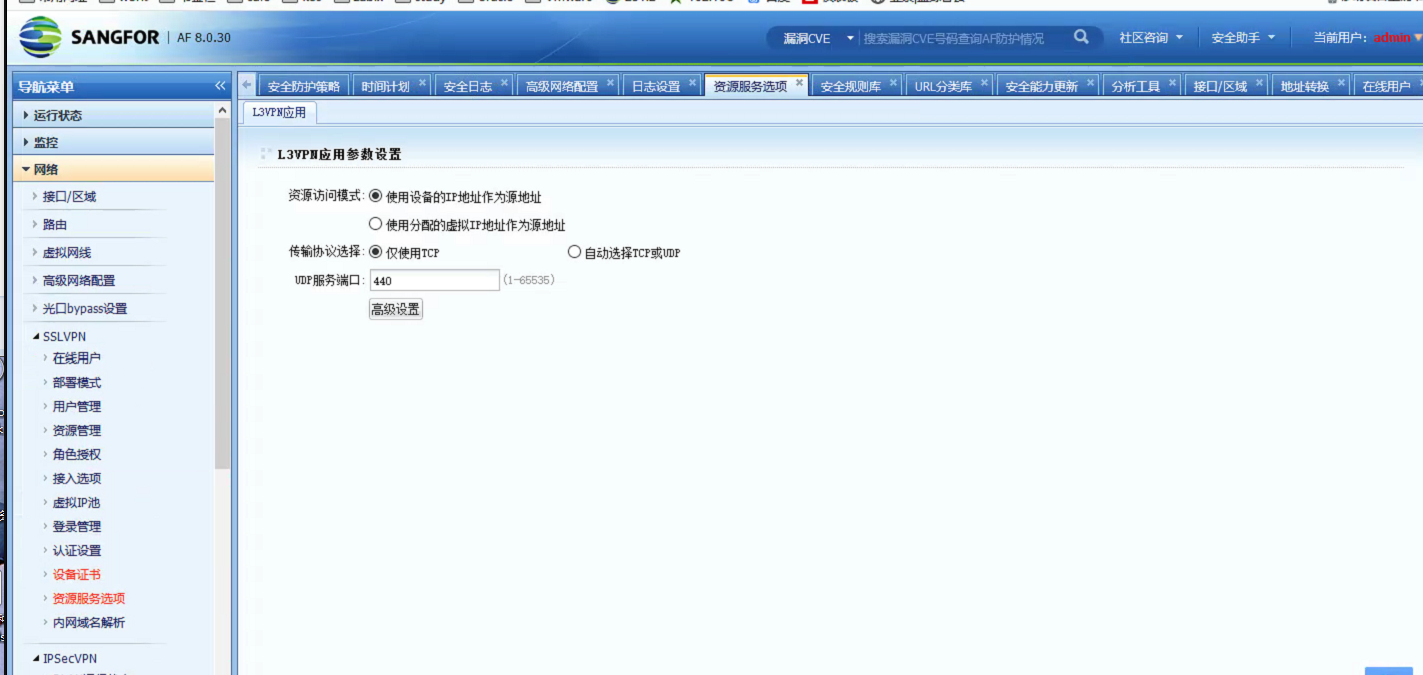
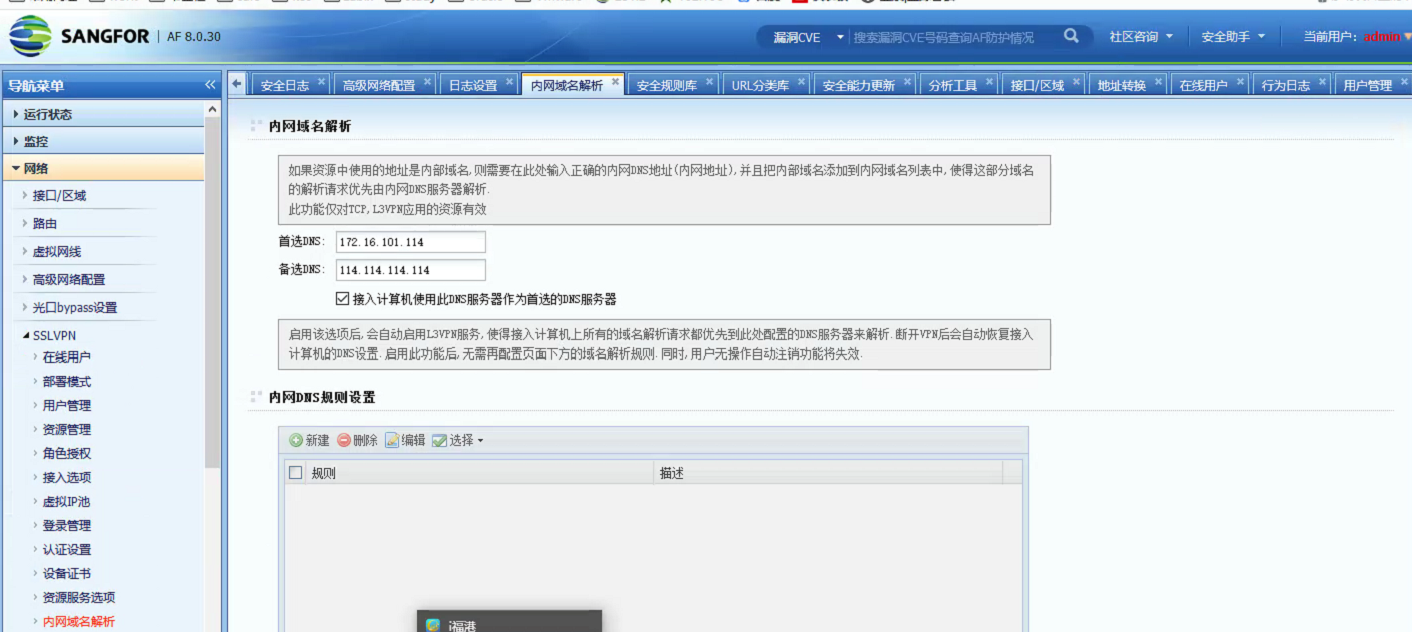
Root cause
From the above, we can conclude that the client terminal accesses the malicious domain name after accessing SSL VPN, which leads to Session Initiation Protocol misjudgment.
solution
First, you need to configure the use of virtual IP to access resources, and then you need to configure a one-to-one corresponding virtual IP for each user, so that you can trace the malicious domain name accessed by the terminal by recording the SSL VPN login log;
Suggestions and Conclusion
It is impossible for Local to perform dangerous actions without reason. It is necessary to check the configuration of Source NAT and Local own attack functions. Common Local scanning functions are shown in the attachment.

Instructions on how to disable the automatic scanning function on the Local
(875 KB)
Original Link
https://support.sangfor.com.cn/cases/list?product_id=13&type=1&category_id=1048&isOpen=true