[AF] Some malicious domain names accessed unblocked DNS Services and were whitelisted
Problem Description
The customer was notified that the intranet accessed a malicious domain name, but AF did not record the interception
Effective troubleshooting steps
-
Sensitive DNS server in the customer's intranet. Check that the malicious domain name redirection function is normally enabled. AF has a botnet interception Logs, but there is no malicious domain name log record that has been reported.
-
Confirm the Network environment. All Internet traffic passes through Local. The reported source IP is the outbound IP of the Local. Confirm that the malicious traffic is allowed by AF. Check whether the malicious domain name has been included in the rule library.
-
The customer's intranet has Session Initiation Protocol. Through Session Initiation Protocol log analysis, it is found that a DNS server is resolving the corresponding malicious domain name at the corresponding time, and this source DNS is in the AF Whitelist;
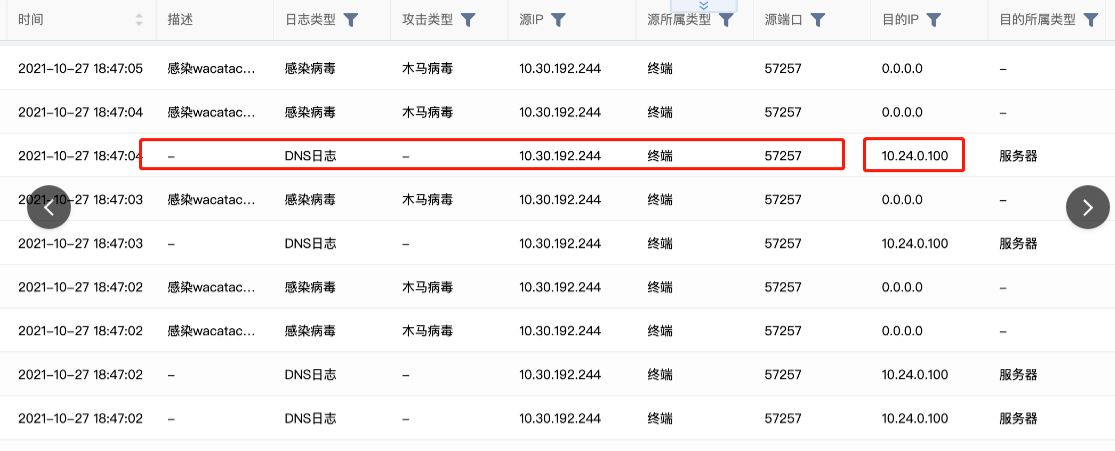
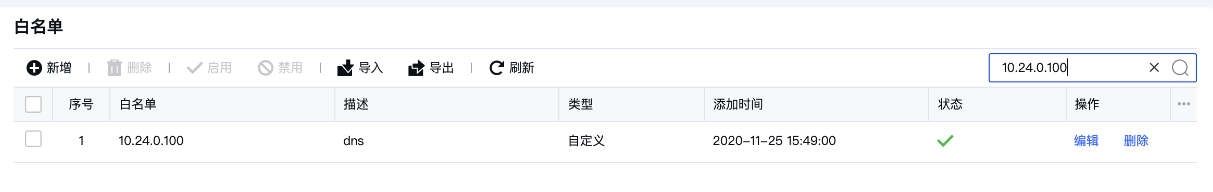
- The malicious domain name Medium the analysis log is indeed the content reported. After deleting the DNS Whitelist, the interception is normal
Root cause
Sensitive multiple DNS Services in the customer's intranet, and one of them is whitelisted, which results in the use of this DNS Services to resolve malicious domain names without being blocked.
solution
After deleting the whitelisted DNS server address, the malicious domain name access action was blocked normally.
Suggestions and Conclusion
If Sensitive multiple DNS in the customer's intranet, you need to confirm the situation of multiple DNS
If you want to test whether the malicious domain name can be blocked in the intranet, you must obtain the customer's consent if you test it on a PC.
Original Link
https://support.sangfor.com.cn/cases/list?product_id=13&type=1&category_id=1400&isOpen=true