[AF] Source and destination IP inversion in IPS client protection log
Problem Description
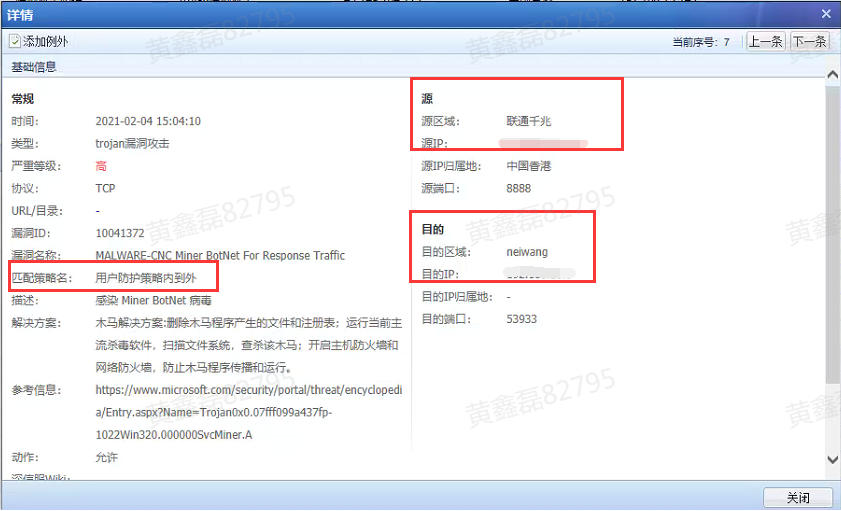
The customer checked the IPS log and found that the attack source was the external network and the target was the internal network, but this attack flow matched the user protection policy from inside to outside.
Effective troubleshooting steps
-
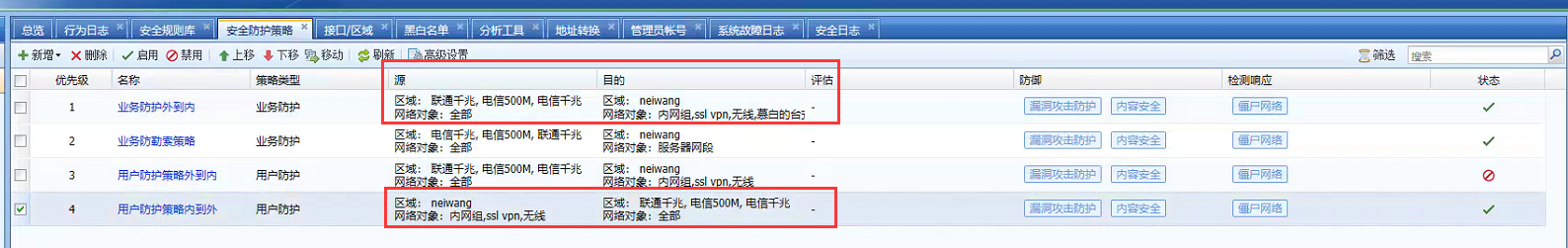
Check the security protection Policies and confirm that the direction of Policies configuration is correct with Objects Network object. The specific configuration is shown in the figure below:
-
Our user protection Policies protects the intranet client. That is to say, in the logic of our AF, if the user protection policy is matched, then the intranet terminal is the object we protect;
-
So logically speaking, the object we are protecting is not the source of the attack, it must be the target object to be protected. Even if the attack flow is from the intranet terminal to the external network, if the user protection strategy is matched normally, then our log display will also show the terminal as the target of the attack and the external network as the source of the attack.
-
It can also be understood that a normal intranet terminal is unlikely to attack the external network for no reason. In other words, it can be determined that the external network first implanted a virus into the terminal, causing the terminal to attack the external network. Therefore, in the client protection Medium in user protection, it will be shown that the attack source is the external network and the attack target is the intranet.
Root cause
AF's IPS client protection log will display the source and destination IP in reverse order.
solution
It is not a display problem. Just explain it to the customer after understanding it.
Suggestions and Conclusion
If you are unsure about this kind of Logs display problem, you can ask the customer Obtain detailed Logs and ask the expert to confirm.
Original Link
https://support.sangfor.com.cn/cases/list?product_id=13&type=1&category_id=1127&isOpen=true