[AF] SSL VPN resources cannot be accessed in multiple penetration scenarios
Problem Description
The firewall deployed with a Virtual wire has a Management Interface connected to the downstream switch using the SSL VPN function. After the configuration is completed, the resources cannot be accessed.
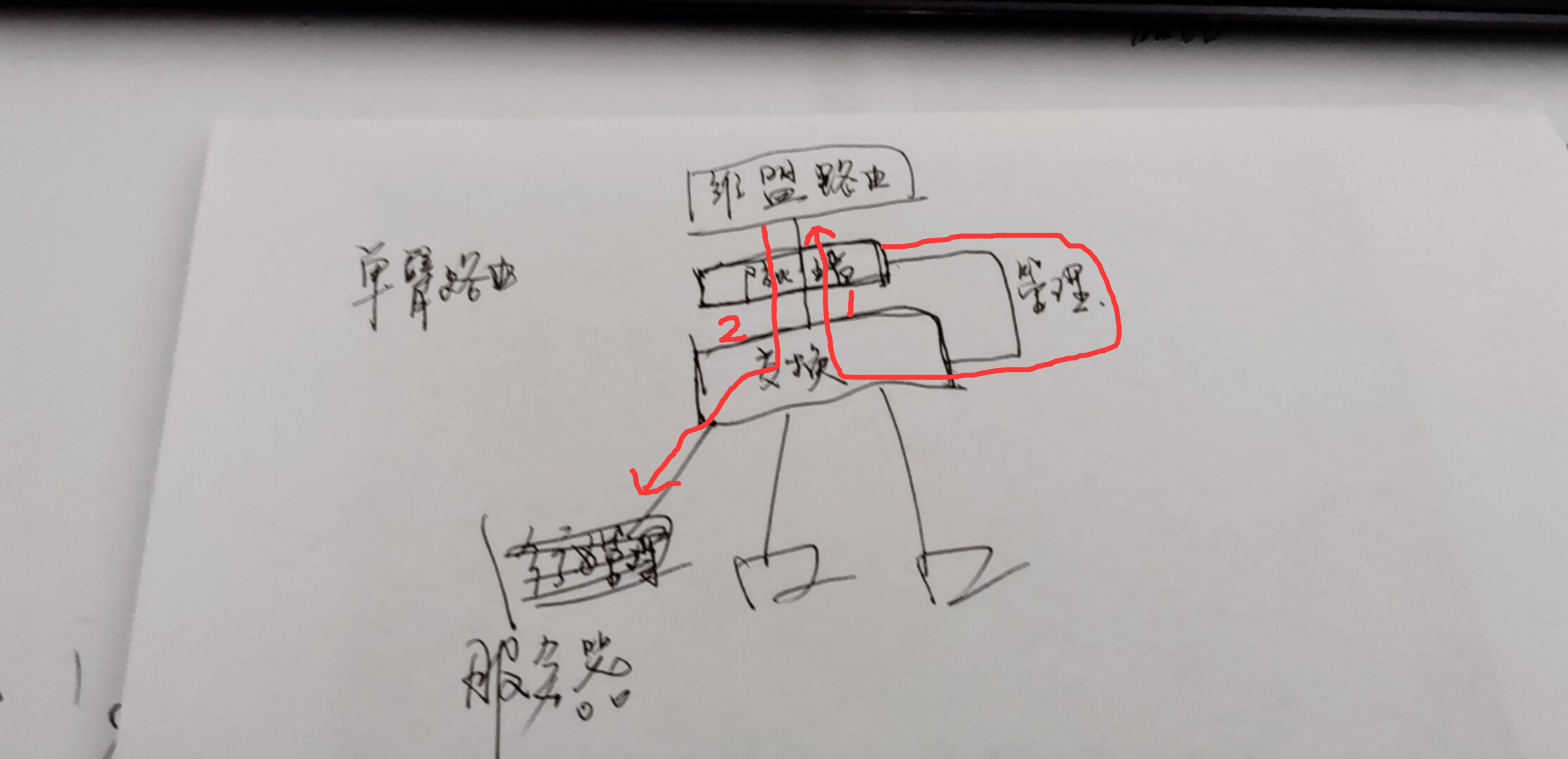
The topology and data flow are shown in the figure below. The Virtual wire port of the downstream switch is eth3, and the virtual network port of the upstream Layer 3 is eth2:
Effective troubleshooting steps
- The customer configures the device LAN port IP to access the intranet resources. The Local itself can access the intranet server, but after the SSL VPN user connects, the Source NAT is converted from the AF Tun port to the LAN port and then converted to the LAN port address, and the access fails;
- After capturing the blocked data packets and analyzing them, we found that the data was stuck at the eth3-eth2 node. After enabling Layer 2 direct access (with the customer's consent), data communication was normal. This basically shows that the data was intercepted due to multiple penetrations.
- After capturing the packets again, we found a complete data flow: Tun port – LAN port – switch – eth3 – eth2 – Layer 3 – eth2 – eth3 – switch – server. This confirmed that the data was blocked because it passed through the device three times.
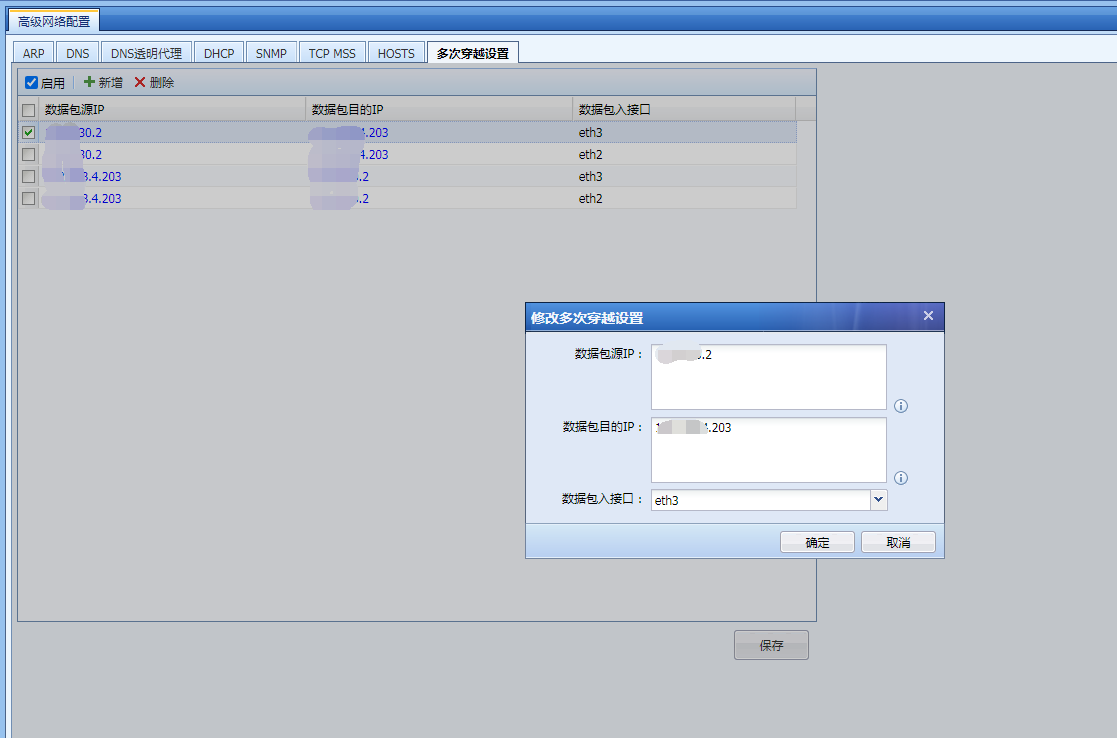
- The customer was not convenient to correct the topology. We communicated with the customer and assisted in configuring multiple penetrations. The second layer released the data that passed through the device twice. After the configuration was completed, the SSL VPN was connected and the access to resources was normal. The configuration is shown in the figure below:
Root cause
Data passes through Local multiple times, causing Local loss and data failure.
solution
After sorting out the data flow, AF8.0.9 and above versions can directly configure multiple penetration solutions. Lower versions need to be upgraded to AF8.0.9 first (the upgrade will Restart the device, so it is recommended to do it during the off-peak period of business)
Suggestions and Conclusion
When encountering such a scenario of suspected multiple penetrations, you must clarify the topology, sort out the data flow, and perform more packet capture analysis.
Original Link
https://support.sangfor.com.cn/cases/list?product_id=13&type=1&category_id=1093&isOpen=true