【SSLVPN】SSL VPN device vulnerability – TLS Version 1.0 Protocol Detection on port 4430
Issue Description
SSL VPN device vulnerability – TLS Version 1.0 Protocol Detection on port 4430
Error/Warning Information
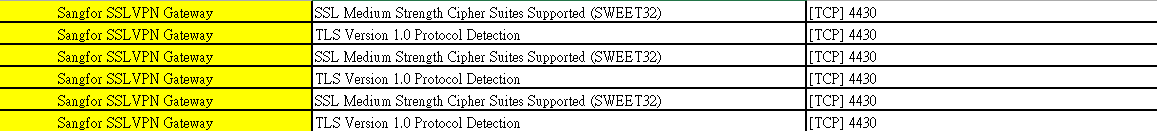
Handling Process
- Checked on device app version verified whether there is patch exist
- Need to apply the following patch on SSL
20210517_CTI-Support_M5.0-M7.6.9R1_TDCommon_4430_sweet32_Patch
20210617_CTI-Support_M6.3R1-M7.6.9R1_TDComClose4430TLSv1.0
Root Cause
Device vulnerability
Solution
Apply the following patch
20210517_CTI-Support_M5.0-M7.6.9R1_TDCommon_4430_sweet32_Patch
https://download.sangfor.com/Download/Product/SSL/Patch/20220218_CTI-Support_M5.0-M7.6.9R2_TDCommon_4430_sweet32_Patch.ssu
20210617_CTI-Support_M6.3R1-M7.6.9R1_TDComClose4430TLSv1.0
https://download.sangfor.com/Download/Product/SSL/Patch/20210617_CTI-Support_M6.3R1-M7.6.9R1_TDComClose4430TLSv1.0.ssu